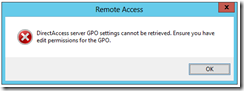
Here is the scenario: You logon to your shiny new DirectAccess server, launch the Remote Access Management Console and click CONFIGURATION from the action pane. A few seconds later you are greeted by the following message
DirectAccess server GPO settings cannot be retrieved. Ensure you have edit permissions for the GPO.
You frantically review your group policies and find that the DirectAccess Server Settings policy is available and applied to your DirectAccess server.
What the? (head banging start here)
The Root Problem
The message is misleading. The real problem is the DirectAccess Client Settings policy!
What is really happening (probably)
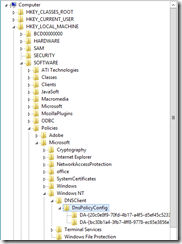
If you have an Organizational Unit (OU) based active directory system, you have probably moved the DirectAccess Client Settings policy to the appropriate OUs so the appropriate workstations and laptops receive the policy.
I.E. something like this (where the policy applies to the HQ/Remote OU):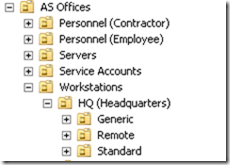
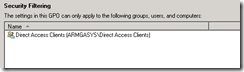
In doing so, you very likely removed the security filtering group the policy was associated to.
It turns out this is a very bad thing in the world of DirectAccess. The DirectAccess Client Settings policy must be available to the DirectAccess server… but should never be applied to the DirectAccess server . In short, DirectAccess computers can only be identified via security filtering and *not* by assigning the policy directly to OUs.
UGH!
So, how do I fix this?
- Link the DirectAccess Client Settings policy to the top level of active directory OUs and not to individual OUs
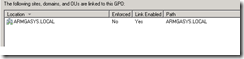
- Filter where the DirectAccess Client Settings policy gets applied via a security group.
(Remember, you don’t want to apply this policy to your DirectAccess server… or any other servers for that mater!)