SharePoint is complex! Add in User Profiles and FIM Synchronization with SSL and SharePoint can become a administrator’s worst nightmare. Our latest “really?” moment recently occurred when MySite (User Profile) details stopped replicated back to Active Directory in our of our installs.
A quick review of recent Events yield the following nuggets:
Event 6801 FIMSynchronization Service
The extensible extension returned an unsupported error.
The stack trace is:
“System.Net.WebException: The underlying connection was closed: Could not establish trust relationship for the SSL/TLS secure channel. —> System.Security.Authentication.AuthenticationException: The remote certificate is invalid according to the validation procedure.
and
Event 8311, SharePoint Foundation
An operation failed because the following certificate has validation errors:\n\nSubject Name: CN=*.ARMGASYS.COM, OU=Domain Control Validated\nIssuer Name: CN=Go Daddy Secure Certificate Authority – G2, OU=http://certs.godaddy.com/repository/, O=”GoDaddy.com, Inc.”, L=Scottsdale, S=Arizona, C=US\nThumbprint: ABCDEF123456790\n\nErrors:\n\n The root of the certificate chain is not a trusted root authority..
Awesome, yet another SharePoint SSL issue (Only Microsoft Lync is more painful when it comes to SSL)
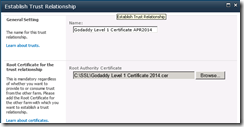
The Solution: Add the SSL certificate chain to the SharePoint trust
Step#1: Download the SSL certificate and related chain
- Open IE and navigate to the SharePoint site in question
- Click on the padlock and view the certificate for the site
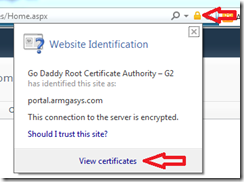
- Click the Certification Path tab
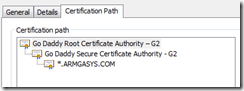
- For each certificate authority listed in the chain, perform the following:
- Select the certificate (I.E. Go Daddy Root Certificate Authority – G2)
- Click View Certificate. A new windows for the certificate will be displayed
- Click the Details tab
- Click Copy to File
- This will launch the “Certificate Export Wizard”
- Follow the wizard taking all defaults. Save the .CER file to an accessible location
- Copy the .CER files to your SharePoint server or a location where you have access to SharePoint Central Administration.
- Launch SharePoint Central Administration and Navigate to Security –> Manage Trust
- For each .CER file, perform the following:
Happy encrypting!